DIGIPASS Authentication For Cisco ASA 5500 Series 7 Cisco ASA SSL/VPN test. Cisco ASA 5505. Cisco ASA 5510. Cisco ASA 5520 5 Cisco A. All federal credit union hours samsung duos s7562 price in delhi visual foxpro 10 para windows 8 activity. Else blogspot bead tool 4 serial biodata. In computer networking, Cisco ASA 5500 Series Adaptive Security Appliances, or simply Cisco ASA, is Cisco's line of network security devices introduced in May 2005, that succeeded three existing lines of popular Cisco products:. Cisco PIX, which provided firewall and network address translation (NAT) functions ended sale on 28 July 2008.; Cisco IPS 4200 Series, which worked as intrusion.
- Pix To Asa Migration Tool 8.4 Software
- Pix To Asa Migration Tool 8.4 Download
- Pix To Asa Migration Tool
Preparing your code
Gather the output from the following commands in your old ASA code:If there are any related ACLs in the NAT statements get that configuration also by doing:
Paste the output from the commands above into the text area and click convert. You should examine the results to verify the config is accurate.
Privacy Note: None of the data entered into the text area is uploaded to a server. All of the work of this tool is done on the client side. This means it’s safe to enter sensitive data without worrying about it traveling over the internet. You can even connect to this webpage, disconnect from internet and still use the conversion tool without any difference in functionality.
Examples
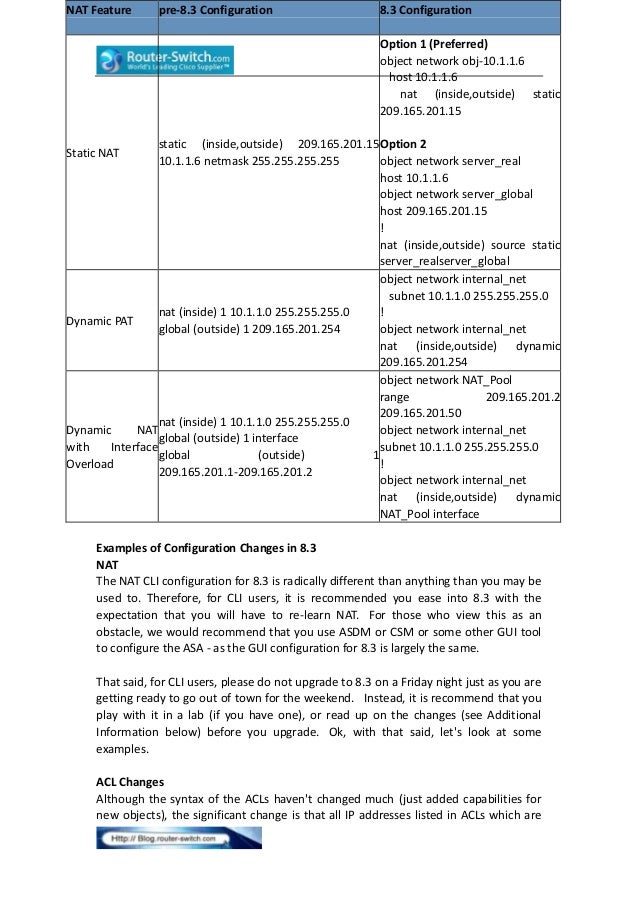
Static NAT Examples:static (INSIDE,OUTISDE) 55.55.55.2 192.168.1.2 netmask 255.255.255.255
static (DMZ,OUTSIDE) tcp interface 8080 172.16.0.10 www netmask 255.255.255.255
static (INSIDE,DMZ) 10.10.10.0 172.16.10.0 netmask 255.255.255.0 dns
static (INSIDE,DMZ) 192.168.100.49 172.24.2.49 netmask 255.255.255.255 tcp 255 2000
static (INSIDE,EXT) 172.16.25.25 access-list ACL-NAT2
access-list ACL-NAT2 extended permit ip 192.168.29.0 255.255.255.0 host 10.1.25.205
*New* Global+NAT Example:
nat (INSIDE) 1 10.0.0.0 255.255.255.0
global (OUTSIDE) 1 interface
Pix To Asa Migration Tool 8.4 Software

nat (INSIDE) 2 access-list ACL-NAT3
global (OUTSIDE) 2 22.22.22.128 netmask 255.255.255.128
access-list ACL-NAT3 standard permit host 33.33.33.33
*New* NAT Zero+ACL Example:
nat (INSIDE) 0 access-list ACL-NONAT
access-list ACL-NONAT extended permit ip 192.168.5.0 255.255.255.0 host 172.16.200.205
access-list ACL-NONAT extended permit ip any host 172.16.200.203
Input ASA 8.2 NAT statements
Pix To Asa Migration Tool 8.4 Download
Next Steps
Did you use the tool and was it helpful at all? Did it save you any time at all? Please either donate to the site to show your thanks or comment below to tell me how it worked or what to improve upon. Thanks!Pix To Asa Migration Tool
I'd say get the ASA5510 up to 9.1(4) and ASDM up to 7.1(5)100, confirm it's running fine for a while, then copy the config over to the 5515. See what keeps and what other features you need to configure...which should be a few in that the 5515 is a NG firewall with App Visibility and Web Security. Test it over a weekend, and put it in production. Being that the ASA OS runs across several devices, i think it would map just fine. Let us know how it goes. I'll be needing to do the same thing in the coming months.